“As I understand it, the reason the money mill was so hard to detect, and the reason it is so hard to trace the illegal transactions even now when we are fully aware of their existance, is that the scoundrel behind this has used computers to automate his attack. It seems that nobody anticipated a carefully choreagraphed and yet still massive attack on our banking system. After all, the larger the attack, the harder it is too coordinate and manage… unless you use computers to process hundreds of thousands of forged checks faster than you can blink.”
Fisk hopped out of his chair and walked to the front of his desk. He clasped his hands behind his back and paced briskly in front of his desk. Agnes was still seated in the chair. She uncrossed her legs to make more room for Fisk to walk between her and the desk. Jonny stood over by the window. I still had not stepped more than a couple of paces into the room and stood behind Agnes with one hand resting on the back of the chair.
“It is ingenious really,” continued Fisk. “The same computers that allow us to process millions of bank transactions in a day, also allow the hacker to create millions of forgeries in a day. By making most of them decoys, he makes our task of tracing the money he borrows next to impossible. On top of that, we can’t even distinguish a bogus EFT from a legitimate one!”
He threw his hands up in despair. Then, without missing a beat he spun on his heels and walked back across the room with his hands once again clasped behind his back.
“What we must do is beat him at his own game. Let’s turn the tables. We will use computers as a tool against him. He uses computers to automate a highly coordinated and massive attack on our banking system; we use computers to track the money through the system.”
“Uh… Sir?” Jonny gently interrupted. “We can try, but that probably won’t work.”
Fisk stopped walking. He said nothing but Jonny had his full attention. Jonny gave a quick sideways glance in my direction, took a deep breath, and explained. “We have another program that does as you suggest, but it is a long shot. It works with recorded EFT data and follows the money through the system. By starting from a payment that we know is counterfeit, and then tracking money into and out of that account, we hope to find other counterfeits. If we can string together enough counterfeit payments, we should be be able to trace the money into a bank account that the hacker is using to collect interest.
“This is not an easy thing to do. The counterfeits are perfect forgeries and are mixed in with legitamate traffic. The amount of EFT traffic along any given path, even through fairly inactive accounts, is very large. It is a pain-staking and labor-intensive task to investigate the validity of each EFT as we trace through the graph.”
“Graph? What graph?” asked Fisk.
“Sorry, Sir. That is a computer science term that Carl has taught us. It is an abstract data structure — a way of organizing data in computer memory. A graph is a set of nodes and arcs. Arcs connect one node to another node. The nodes represent bank accounts. The arcs represent funds transfers. The direction of the arc represents the direction of the transfer. When there are several payments between two accounts, there are several arcs, one for each payment.”
Fisk nodded his head slowly. It was apparant that he was only half-following Jonny’s explanation. Jonny glanced at me, then Agnes. He strode over to the desk and took a pencil out of Fisk’s pencil-holder. Next he pulled a crumpled envelope out of the waste-basket. He quickly sketched a graph for Fisk.
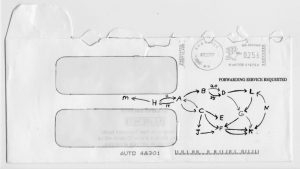
“See. Now suppose I trace a path in the graph starting here at point A. I have two choices: I can go to node B or C. Suppose I choose C. Now I have four choices, one of which is to go back to A. Just to keep things interesting, I’ll go back to A, and then from there I’ll take the arc to B. At node B there are two out-going arcs, both going to D. I’ll take the arc labelled as twenty dollars. From D, I can go to G, then K, and so on.”
Jonny paused while he counted up the arcs in his example. “Even in this small graph, with only about twenty arcs, there are dozens of possible paths. Now imagine we have the full EFT graph, which has hundreds of thousands of new arcs every day. Then possible paths number in the trillions. Or more. To make things even more complicated, when the paths get very long it is difficult to recognize when you re-visit the same node; you can go around in circles without even realizing it! This is because the EFT graph has cycles. This is the whole point behind the money mill — the millwright is using cycles in the graph to skim off interest payments from banks. Even if we had a way to quickly identify the forgeries, we still would not have a good way to track the money. There are so many forgeries in the network today that even after we single out only the forged arcs in the graph and trace those, the graph is still too complex. There are too many bogus paths. This is what it means to mount a massive attack against the system.”
